In today’s world, where everything is online, the need for online privacy and security is at an all-time high. One way to achieve online privacy is by using a Virtual Private Network or VPN. A VPN is a technology that provides a secure and private network connection over the internet.
Defining a Virtual Private Network (VPN)
A virtual private network (VPN) is a technology that provides a secure and private network connection over the internet. It creates a private network by encrypting and tunneling internet traffic through a remote server, allowing users to access the internet securely and privately. VPNs are commonly used to protect internet users’ online privacy, allowing them to hide their IP address and online activities from their internet service provider and other third parties. They are also used by businesses to provide remote employees with secure access to the company’s network and resources.
How a VPN work
A virtual private network (VPN) works by creating a secure and encrypted connection between a user’s device and a remote server operated by the VPN provider. Here is a simplified explanation of how a VPN works:
- User initiates a connection – The user launches the VPN client software or app and selects a server location to connect to.
- Encryption – The user’s device encrypts all the internet traffic that is sent over the VPN connection using a secure encryption algorithm. This makes it impossible for anyone to intercept or read the data that is being transmitted.
- Tunneling – The encrypted traffic is then sent over the internet to the VPN server, which decrypts the traffic and sends it on to its final destination.
- IP Address – When the traffic exits the VPN server, it appears to be coming from the VPN server’s IP address, not the user’s original IP address. This helps to protect the user’s online privacy and identity.
- Decryption – The website or application that the user is accessing receives the decrypted traffic and sends its response back through the VPN server.
- User receives the response – The VPN server re-encrypts the response and sends it back to the user’s device.
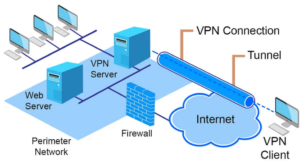
By using a VPN, users can surf the web securely and privately without worrying about hackers, government surveillance, or other third-party entities tracking their online activities. Additionally, businesses can use VPNs to securely connect their remote employees to their network and resources.
Benefits of using a VPN
Using a virtual private network (VPN) provides several benefits for both individuals and businesses.
The key benefits of using a VPN includes;
- Security – One of the main benefits of using a VPN is increased security. VPNs encrypt internet traffic, making it difficult for hackers, governments, and other third parties to intercept or read data. This is especially important when using public Wi-Fi networks, which are often unsecured and pose significant security risks.
- Privacy – VPNs help protect users’ online privacy by hiding their IP address and other identifying information from third parties. This can help prevent online tracking, targeted advertising, and other forms of online surveillance.
- Access to restricted content – Some websites and online services are only available in certain regions or countries. VPNs allow users to connect to servers in different locations, giving them access to geo-restricted content and services.
- Remote access – VPNs can be used by businesses to provide remote employees with secure access to the company’s network and resources. This allows employees to work from anywhere while still maintaining a secure connection to the company’s systems.
- Cost savings – VPNs can help businesses save money by reducing the need for expensive leased lines or dedicated network infrastructure. Instead, employees can use secure VPN connections to access the company’s network from anywhere in the world.
Types of Virtual Private Networks
There are several types of virtual private networks (VPNs) available, each with its own unique features and benefits. Here are some of the most common types of VPNs:
- Remote Access VPN – A remote access VPN is designed to allow remote workers to securely connect to a company’s network. Remote access VPNs typically use encryption to protect data transmitted over the internet, and they often require authentication to ensure that only authorized users can access the network.
- Site-to-Site VPN – A site-to-site VPN, also known as a router-to-router VPN, is used to connect two or more physical networks together over the internet. Site-to-site VPNs are often used by companies with multiple offices in different locations, and they can be used to securely share resources between those offices.
- Mobile VPN – A mobile VPN is designed to provide secure access to a company’s network from mobile devices such as smartphones and tablets. Mobile VPNs often use technologies such as Secure Sockets Layer or IPSec to provide encryption and authentication.
- Cloud VPN – A cloud VPN is a type of VPN that is hosted by a cloud service provider. Cloud VPNs are often used by companies that want to provide secure access to their network for remote workers or partners without having to manage their own VPN infrastructure.
- Secure Socket Layer VPN – An SSL VPN, also known as a web VPN, is a type of VPN that uses Secure Sockets Layer (SSL) encryption to provide secure remote access to web-based applications. SSL VPNs are often used by companies that have a lot of web-based applications that need to be accessed securely by remote workers.
- IPSec VPN – An IPSec VPN is a type of VPN that uses Internet Protocol Security (IPSec) encryption to provide secure network-to-network or remote access connections. IPSec VPNs are often used by companies with multiple offices in different locations or by remote workers who need secure access to the company’s network.
Choosing a VPN provider
When choosing a VPN provider, there are several factors to consider which includes;
- Security – The VPN provider should use strong encryption to ensure that an organization’s data is protected.
- No-logging Policy – The VPN provider should have a strict no-logging policy. This means that they do not keep any logs of organization’s online activities.
- Server Locations – The VPN provider should have servers located in the countries where a business needs to access content.
- Speed – The VPN provider should have fast servers to ensure that business’s internet connection is not slowed down.
- Customer Support – The VPN provider should have good customer support to help a business with any issues that it might encounter.
Conclusion
In today’s world, where online privacy and security are at risk, using a VPN is one of the best ways to protect organization’s online activities. A VPN provides a secure and private network connection that encrypts organization’s internet traffic, ensuring that organization’s data is protected from prying eyes.
Audit plays a major role in reviewing and evaluating the VPN’s configuration, policies, and procedures to ensure that they are in compliance with industry best practices and regulatory requirements. Audit also reviews the service provider’s ability to meet an organization’s online privacy and security needs.
Reach out to us through our contacts below and get an assurance on the internal control levels your organization’s virtual private network.
Mayfair Business Centre,2nd Floor
Off Parklands Road.
P.O. Box 6358-00100 Nairobi,
+254 715 248882 | +254 733 533449
info@mgkconsult.co.ke | www.mgkconsult.co.ke

